Blockchain technology presents numerous benefits and opportunities for individuals, governments, and organizations, with smart contracts and decentralized applications (DApps) facilitating global data use and streamlining processes. In some cases, however, a blockchain's transparency might actually hinder adoption, as sensitive information may not be adequately protected. The most common types of sensitive information fall under these categories:
- Sensitive personally identifiable information (SPII) such as biometric identifiers, passport numbers, etc. Privacy laws like the European GDPR commonly protect these.
- Financial information such as account information, transaction reports, annual audits, payments metadata, etc. Many common security practices also exist, such as the Payment Card Industry (PCI) compliance standards.
- Protected health information (PHI) such as health records, lab results, medications, etc. Laws like the US HIPAA commonly protect these.
- Intellectual property (IP) such as patents, copyrights, design rights, trademarks, service marks, trade secrets, know-how, etc. Commercial law in the relevant jurisdiction commonly protects these.
Until recently, the industry’s response has involved creating privacy solutions that can lack regulation compliance. There needs to be a middle ground between transparency and data protection, a solution that enables composable privacy, where the application developer has the freedom to determine the level of data confidentiality required for a specific use case. This is where the Midnight blockchain’s smart contract protocol comes in.
Read on to learn more about Midnight and how it enables wider blockchain adoption through regulation compliant data protection.
What is Midnight?
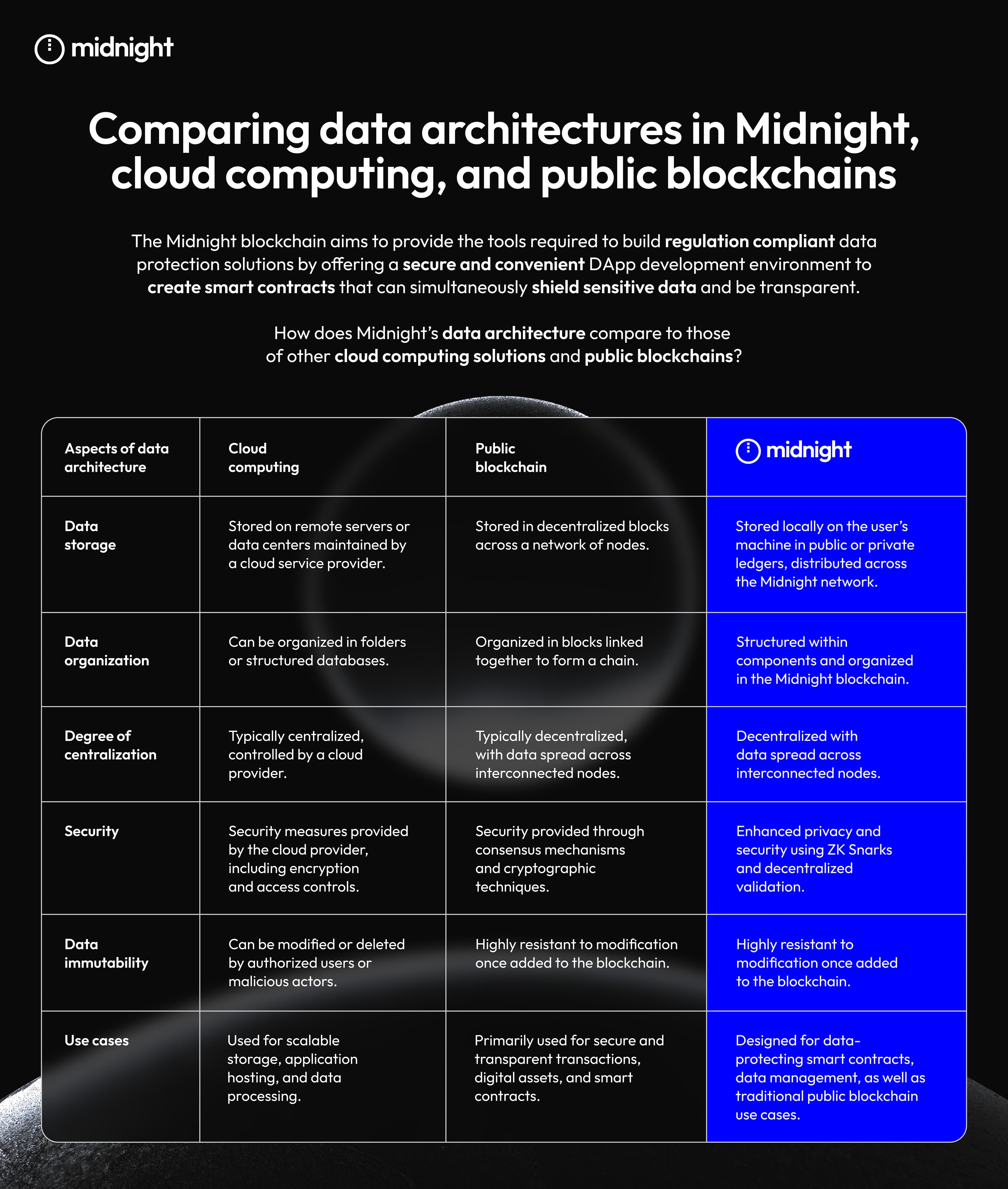
The Midnight blockchain, developed by Input Output Global (IOG), will provide everyone with the tools required to build regulation compliant data protection solutions. Midnight will offer a secure and convenient DApp development environment to create smart contracts that can simultaneously shield sensitive data and be transparent.
Midnight’s set of development tools will simplify DApp creation and enhancement by enabling developers to focus on implementing useful features.
Midnight leverages data-protecting smart contract research and zero-knowledge succinct non-interactive arguments of knowledge (ZK Snarks) that will enable DApp users to make provable assertions about themselves without sharing identifiable information.
The blockchain’s data-protecting features will enable:
- Execution of commercial transactions with minimal risk of theft or malicious interference
- Optimizing app developers’ compliance burden through use of proofs in place of transmission of sensitive information
- Free expression of views without fear of censorship.
Midnight’s benefits and use cases
Public and private blockchains have limitations when it comes to wider adoption, but Midnight will offer the best of both worlds, where it enables the creation of DApps with benefits such as:
- Data protection
- Assurance of data integrity
- Scalability to ensure smooth user experiences and accommodate growth without compromising performance
- Creating a verifiable and decentralized Web3 environment
- Self-sovereign identity management
- Enhanced developer experience with simple and accessible integration of ZK Snarks
- Potential reduction of compliance costs and system maintenance for organizations with reduced need to capture and store customer data.
Potential DApp use cases include:
- Shareable know your customer (KYC) credentials, that enable individuals or institutions to validate themselves without the need to pass further documentation
- Decentralized credit scoring, with credit scores assigned to decentralized identifiers, preventing leakage to malicious actors
- Decentralized anonymous voting, with voters able to prove that they are qualified to vote, and have not voted fraudulently, without disclosing any additional information
- Medical history systems preserving patient confidentiality.
Learn more about Midnight
As a data protection blockchain, Midnight's mission is to provide DApp-building tools that enable developers to safeguard sensitive commercial and personal data, ensuring that the essential freedoms of association, commerce, and expression remain intact for developers, companies, and individuals.
Learn more from the Midnight website and sign up to get all the latest news and updates.




