Scavenger Mine recap
Scavenger Mine, the second phase of the NIGHT token distribution, closed at midnight on November 20. With over 4.5 billion NIGHT claims registered across more than 8 million participating addresses, the Glacier Drop distribution is currently the industry's largest based on participating wallets and claim volume.
Midnight’s Glacier Drop, the multi-phase model for its native asset, NIGHT, sets a new standard for token distribution. The structure combines a broad, community-driven allocation with mechanisms designed to increase fairness and systemic integrity. This includes the gradual unlocking (thawing) of claimed tokens, which inspires the name Glacier Drop.
What’s next in the NIGHT token distribution
The NIGHT token distribution will continue with:
- Redemption Period (450 days): During this phase, claimed NIGHT tokens will gradually unlock or “thaw” in four equal 90 day installments.
- Lost-and-Found (4 years): Late claims from original eligible wallets after mainnet launch.
- Exchange-Facilitated Claims (coming soon): Several exchanges (including Kraken, OKX, Bitpanda, and NBX) are working to enable claims for their users. If you held qualifying assets for Glacier Drop on a participating exchange, check with them directly, you may still be able to receive an allocation through their platform.
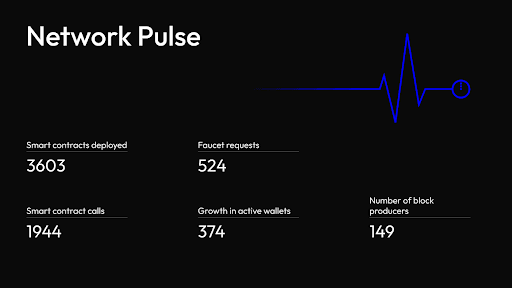
Network pulse
The Midnight ecosystem continued to see steady development throughout October. Developer activity maintained a consistent pace following a concentrated period that included three major hackathons in September and culminated in Midnight's largest-ever in-person hackathon at the Summit on November 19.
Ecosystem: Spotlight on the Midnight Summit
The inaugural Midnight Summit united over 450 builders, developers, and privacy advocates, confirming a shared mission: to build infrastructure for a more private, fair, and equitable digital future. The event, held at the historic Old Royal Naval College, and the three keynote addresses connected the network's foundational philosophy (Why), its strategic roadmap (When), and its core architecture (How) for achieving rational privacy.
Watch the full event livestream to get more insight into all the current activities and the vibrant future of the ecosystem on the Midnight YouTube channel.
Why: Midnight is engineered for rational privacy
In the first keynote address, Midnight Foundation President Fahmi Syed explained that to participate in a transparent, decentralized internet, users often expose all personal data permanently.
Rational privacy moves beyond the binary choice of total exposure or total secrecy. This technical framework uses programmable privacy tools, such as selective disclosure, empowering individual judgment over data handling. Privacy is the network default, and disclosure happens only by choice.
This technology provides the groundwork for core digital freedoms:
- Freedom of association: Individuals connect and build communities while maintaining ownership and control over data.
- Freedom of commerce: Privacy is programmable, enabling new forms of digital exchange.
- Freedom of expression: Tools allow idea-sharing without the chilling effect of permanent surveillance.
The widespread participation in the recent NIGHT token distribution, with over 1 million users and 4.5 billion tokens claimed, signals a profound engagement with the Midnight vision.
Read more in the keynote recap on the Midnight Foundation blog
When: The roadmap to a fully realized mainnet
Input Output Founder Charles Hoskinson framed the network's philosophy through Cooperative Economics, aiming to provide "an extension of what you already have" by allowing Midnight to function as a Layer 2 for all ecosystems.
To answer the question, "wen Midnight," the roadmap outlines the delivery of core network capabilities over four phases, each named for a Hawaiian moon which is explained in more detail in this Midnight Foundation blog.
This roadmap builds on previous generations of blockchain technology to get to Midnight, fourth generation blockchain: "Satoshi gave us good money; Ethereum gave us programmability; Cardano brought the third generation of interoperability, scale and good governance. Midnight gives us our identity and privacy back.”
How: Architecting the network to solve the privacy trilemma
Shielded Technologies CTO Bob Blessing-Hartley explained in his keynote how Midnight is designed to solve the privacy trilemma, reconciling the competing needs of users, developers, and regulators without compromise.
The Privacy Trilemma consists of:
- Privacy: Protecting sensitive data from public exposure on the ledger.
- Programmability: The ability to run complex logic and applications (smart contracts).
- Compliance: The capability to satisfy legal and regulatory requirements (e.g., audit trails, data residency).
Midnight achieves all three simultaneously through four core components: Programmable privacy, cooperative economics, advanced tooling, and governance.
The NIGHT and DUST Cooperative Economic Model
The dual-component economic model aligns incentives and removes friction for user onboarding:
- NIGHT: The native utility token (24 billion supply). It grants governance rights and acts as a generator for the operational resource, DUST.
- DUST: The fuel that powers smart contract execution and privacy-enhancing operations.
DUST is a renewable resource that regenerates over time based on NIGHT holdings, operating on a "recharge" model. "You can take the NIGHT that you claim, and use that to fuel your DApps, so that nobody ever has to pay for a transaction on Midnight to use your application." explained Bob.
This enables self-funding DApps, removing the burden of transaction costs from the end-user and allowing users to transact without sacrificing their governance rights linked to their NIGHT holdings.
Enabling Compliance By Design
Regulatory compatibility is treated as a necessary feature for global adoption. Midnight’s architecture enables selective disclosure, allowing builders to create applications that are compliant for any jurisdiction.
Midnight’s architecture transforms auditability into an active, selective feature, allowing enterprises to adopt blockchain without running afoul of laws like GDPR or HIPAA with rules about how personal data is collected and stored. "Midnight allows you to write data about somebody that doesn't reveal who they are. Therefore, you do not have to forget them," explained Bob.
Midnight provides the tools required to build what was previously impossible: applications that protect freedom, enable commerce, and respect the user by embedding privacy into the core infrastructure. Read the full recap on the Shielded Technologies blog.
Hackathons
The continued momentum of hackathons and community developer events represent critical steps in growing the global builder community and testing the network's technology in real-world scenarios.
Midnight Summit Hackathon
The Midnight Summit Hackathon was a resounding success, establishing a live proving ground for the next generation of privacy-first technology. More than 120 hackers were building on site at the summit in London, with hundreds more participating remotely from around the world. They demonstrated incredible creativity by building innovative, practical solutions that leverage Midnight's programmable privacy.
Hackers competed for prizes across four tracks:
- AI: Focus on building applications that enable confidential inference and verifiable model outputs without exposing raw data.
- Healthcare: Focus on creating solutions for privacy-preserving patient data exchange and ZK-verified compliance.
- Governance and identity: Focus on new systems for private, verifiable participation in governance using selective disclosure and ZK voting.
- Finance: Focus on applications demonstrating ZK-KYC, private settlement, and policy-gated disclosure for compliant finance primitives.
Details on the winning projects will be published soon.
Hacktoberfest debut drives community contributions
The Midnight community recently participated in Hacktoberfest for the first time, successfully launching a small pilot participation in this annual event. The community showed impressive engagement and contributions across the three open-source repositories involved.
The three winners Bochaco, CardanoProphet, and IslandGhostStephanie earned Zealy XP as part of the Midnight ambassador program along with Midnight-branded prizes, for their contributions.
Key contributions included:
- A React guide detailing how to connect a wallet.
- Fixes for reported issues with Cargo Clippy.
- Updates to outdated references in both Midnight Docs and Midnight JS repositories.
Thanks to all participants, reviewers, and supporters who made this debut initiative a success.
Community Survey now closed
Over 500 people participated in the second annual Midnight community survey. The survey saw increased participation from nearly every continent, with significant international growth in responses from Africa, Asia, and South America, representing a diverse range of participants across many different ecosystems. The Midnight Foundation is now analyzing the data, initial insights from the aggregated, anonymized findings will be shared publicly in December. Keep an eye on the Midnight blog for more.
To follow all the latest news and updates across the Midnight Network, join the community on X now.