Developers from around the world came together for the ZK Identity Challenge. From morning in rural Montana to Bali after midnight. Teams from Brazil, Argentina, Switzerland, and Finland came together to showcase decentralized identity solutions using zero-knowledge (ZK) proofs.
Showcasing Midnight’s unique ability to keep secrets on-chain, the challenge focused on private digital identity verification, authentication, and access control. Participation in this hackathon nearly doubled: from four teams in the previous Sea Battle hackathon to seven teams presenting decentralized identity solutions.
Building together and raising the bar
This hackathon saw a mix of returning builders and fresh faces, each bringing different problems and solutions to decentralized digital identity (DID). Some teams focused on real-world compliance, using ZK proofs to streamline KYC and AML checks, while others explored user-owned identity, creating solutions that let individuals prove who they are without oversharing.
There was notable improvement in submissions from some of the returning teams. Participants delivered sharper, more refined projects, demonstrating continued improvement since the last hackathon. The community played a big role too. Defending champions Brick Towers were in the Midnight Discord server answering questions and supporting other hackers. Whatever your experience level, Midnight hackathons are a great opportunity to learn and build with the community.
Functionality
To compete, projects had to showcase Midnight’s ability to enable private, verifiable identity solutions. That meant:
- Using ZK circuits to verify identity without exposing personal data.
- Integrating with the Lace Wallet for secure identity proofs and transactions.
- Building with Midnight’s Compact language, the foundation for smart contract logic.
- Including a user-friendly UI because ease-of-use fosters adoption.
- Mock up off-chain data sources to simulate real-world identity verification.
Judging criteria
All hackathon projects are evaluated on four key areas:
- Technology: How effectively did the project use Midnight’s ZK capabilities? Judges look for strong smart contract design, efficient circuit implementation, and excellent privacy enforcement.
- Innovation: Unique approaches to identity verification stand out. Whether streamlining compliance or enabling new forms of authentication, creative problem-solving and elegant solutions to problems score points.
- Completion: A polished, functional prototype scores higher than an ambitious but unfinished concept.
- Documentation: Clear, structured documentation matters. Someone who has never seen the project before should be able to figure out how to use it.
The winners
#1 - Brick Towers
The defending champions from the previous hackathon Sergey Kisel and Imants Firsts from Brick Towers took home first place with an elegantly-coded solution tackling age-restricted e-commerce. Their project proved a buyer’s legal drinking age without exposing personal data, showcasing how Midnight enables privacy-protecting identity verification.
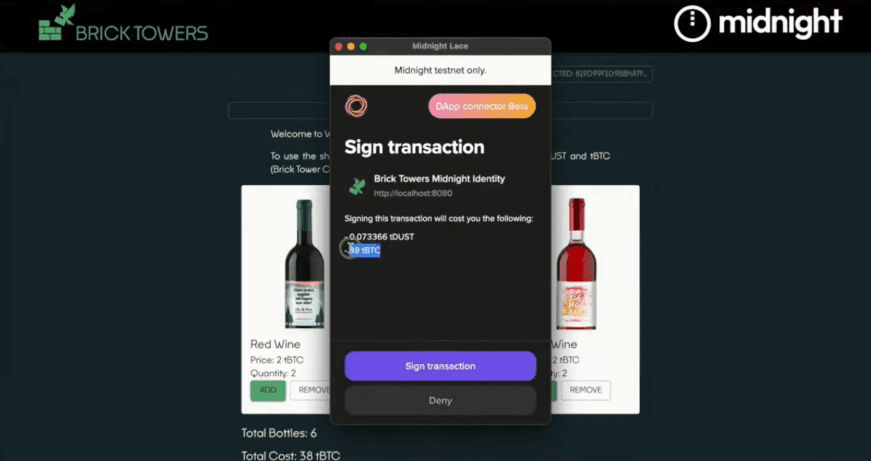
How it works: A customer places a wine order, triggering a transaction recorded on-chain while keeping personally identifiable information off-chain. Instead of uploading an ID, the buyer generates a zero-knowledge proof confirming that they meet the legal drinking age without exposing their birth date or ID number.
If the verification fails, the system notifies the user privately, ensuring that no sensitive information is leaked (and no embarrassing “you’re too young” messages get permanently recorded on-chain).
Once verified, Midnight’s smart contracts confirm the purchase, payment, and age requirement without revealing personal data.
Judges praised the project’s efficient code, strong documentation, and real-world impact. By eliminating the need to store sensitive user data, Brick Towers’ solution not only protects privacy, but also reduces compliance burdens for retailers who often would rather not handle sensitive data in the first place.
Future hackathon participants take note of how this project was delivered: a well-scoped, clear problem-solving approach that delivers on its promises.
Watch their presentation on the Midnight YouTube channel, and check out their code on GitHub.
#2 - Edda Labs
Edda Labs (led by Erick Romero and Tainá Bugs) built a solid foundation for AML Anti-Money Laundering (AML) compliance and jurisdiction-based restrictions for real estate transactions.
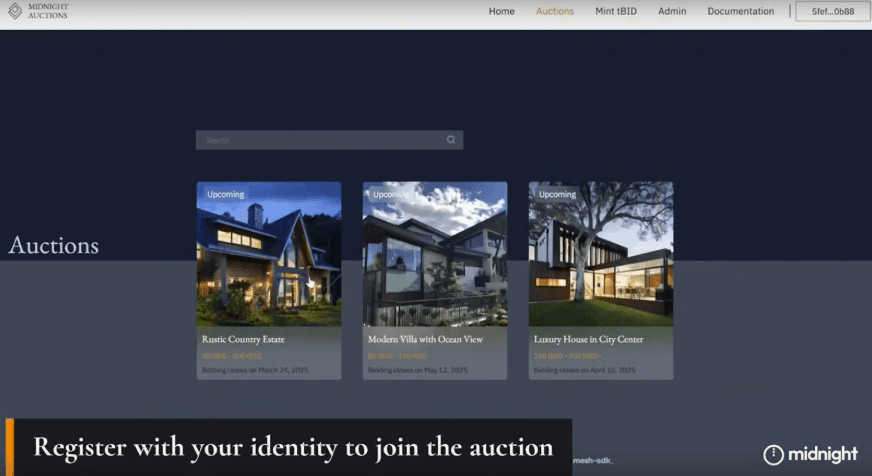
What made their project stand out was a slick, functional demo backed by modular, well-structured code. Their smart contracts handled compliance checks for AML, jurisdiction, age, and certification, ensuring that only verified users could place bids. The system also featured real-time bid verification, requiring users to prove compliance on-chain before participating, demonstrating a seamless, automated approach to trust and security in online auctions.
Future hackathon participants take note: A polished, clearly explained demo makes all the difference when showing off your work (and when the code delivers on your promises).
Watch their presentation on YouTube to see an example of best practices when showcasing a product. Their code is available on Github.
#3 - Fairway
Fairway banked on privacy in a real-world use case for verified national identity in digital finance. Their project linked government-issued IDs with Midnight to generate a soulbound token, which is a type of NFT permanently issued to a specific wallet that cannot be transferred. This token serves as a secure, verifiable proof of national identity.
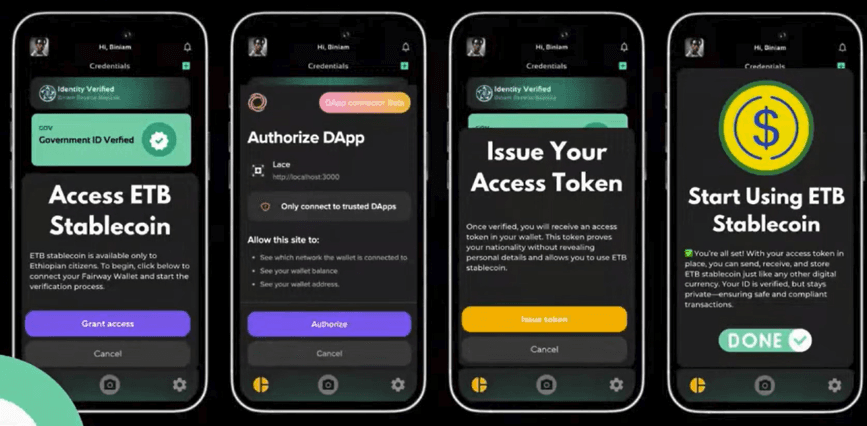
How it works: Users begin by verifying their national ID, after which Midnight generates a private proof of identity stored securely within their wallets. This proof allows for secure, regulation-compliant transactions without exposing personally identifiable information. Judges praised the exceptionally strong use case, but pointed out a key gap: the credentials weren’t fully verified, and some functionality still needed to be built.
Overall the judges indicated it was a very interesting project with promising ideas and practical applications. You can see their presentation on YouTube and their code is available on GitHub.
Honorable mention: Midnames
Midnames impressed judges with an enthusiastic presentation of a mobile-based approach to decentralized identity. Their project scanned NFC passport chips to transform identity data into zero-knowledge proofs.
How it works: The system features three components: a local server, a listening app, and a DApp that validates identity proofs. Their ZK circuit-based validation securely handles passport expiry and age verification, demonstrating a strong technical foundation.
While the concept and execution were impressive, missing smart contract functionality prevented a higher ranking. However, the project’s strong documentation stood out, and judges loved both the enthusiasm and the ideas presented, and said they would love to see further development of this project.
Advice for future hackathon participants
Participate in the community
Engaging with the community can make a difference. Previous winners, like Brick Towers, actively supported newcomers in the Midnight Discord. Take the opportunity to learn from others and share your knowledge.
Starting small and building functional smart contracts and ZK circuits is also key. A polished, fully working DApp will outperform an ambitious but unfinished concept, so focusing on a single, strong use case is often a good place to start.
Create user-friendly documentation
Clear, well-structured documentation makes a project stand out. Top scoring teams explained their work in a way that others could understand and build on. A great project is about accessibility as well as functionality.
Think from the perspective of a new user. Walk through each stage of your DApp, explaining what it does and how it works. Not all users, or even some judges, will have the same level of experience, so clarity is key. Strong documentation ensures that anyone interested in your project, from developers to potential users, can use it easily.
What’s next
When one hackathon ends, another one begins. The Automated Market Maker Challenge (AMM), hosted by ecosystem partners OpenZeppelin, is all about decentralized finance. ZK circuits allow for privacy-enhanced AMM protocols that balance transparency with confidentiality, showcasing how Midnight can bring innovation to the DeFi space. Registration is open from March 10 to April 1st.


